By Sumera Riaz, VP of Cybersecurity
2026 is shaping up to be a transformative year in cybersecurity, especially with disruptors like the upcoming VMWare to VCF 9 October 2027 deadline 🡥 and the widespread adoption of AI.
As Fortinet explained in its 2026 Cyberthreat Predictions report 🡥, this will be a year of cybercrime acceleration with adversaries increasingly operating using a mix of automation, specialization, and AI to launch sophisticated attacks at scale.
But here’s the part many advisors are overlooking:
According to Barracuda, nearly two-thirds of organizations have increased security budgets by more than 25% 🡥, specifically to address increased AI adoption and risk. And over half of large U.S. organizations plan significant spending boosts in 2026 to address evolving threats.
For technology advisors, this signals a rare moment: the ever-expanding attack surface, board-approved budgets, and an urgent need for trusted guidance. So it’s time to throw out the old playbook and start being more intentional about asking critical cybersecurity questions.
In this post, we’ll explore:
- How AI is impacting cybersecurity
- The top services customers are buying
- Tips for starting effective cybersecurity conversations
- Why now is the time to engage customers
It’s Déjà Vu All Over Again with AI
Every new technology moves the world forward—and introduces new security risks.
Security rarely evolves at the same pace as innovation. There is almost always a one-to two-year gap before mature, battle-tested security solutions emerge. In that gap, adversaries move quickly, exploiting vulnerabilities long before organizations are ready to defend them.
Here’s how it usually plays out:
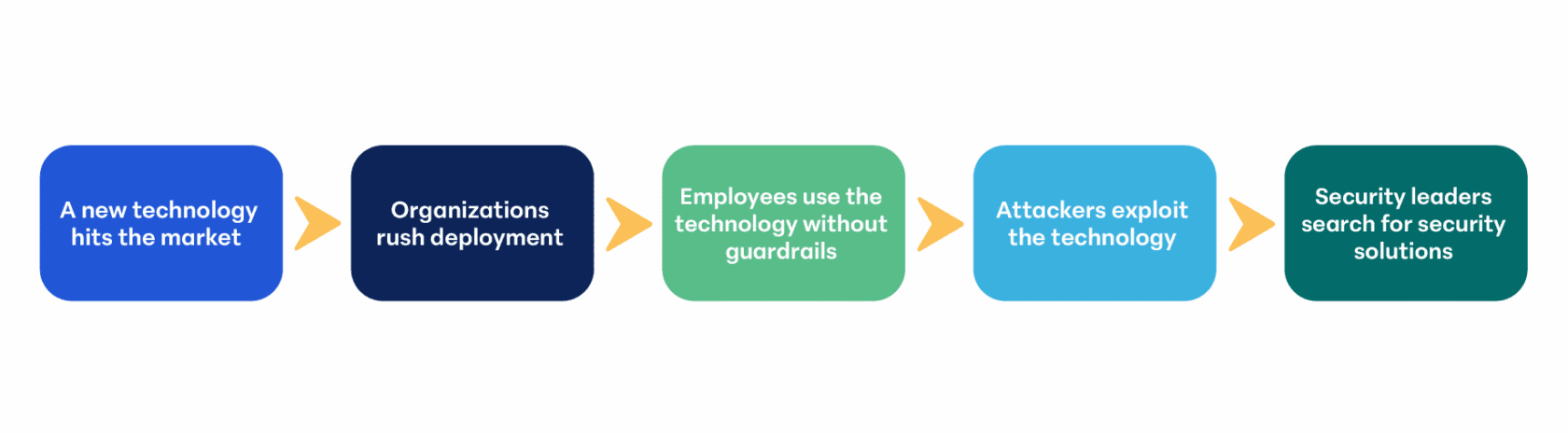
We’ve seen this pattern before. Cloud computing was one of the most disruptive technology transformations of the last decade. It unlocked greater speed, scale, and flexibility—but it coincided with some of the highest cybercrime rates in history.
Between 2010 and 2015, global cloud adoption exploded. During that time, security spending increased by about 50%, while cybercrime grew by 150%. Only after organizations were hit did they invest seriously in cloud security—and once they did, the attack rate began to level out.
The lesson is clear: Organizations that move fast without a security strategy often pay for it later, at a much higher cost.
Today, we’re at that same inflection point with AI.
AI Has Changed the Economics of Cybercrime
AI has lowered the cost of launching sophisticated cyberattacks to near zero.
Threat actors are actively using AI and automation to accelerate attacks. As Fortinet noted, ransomware affiliates can now launch ten attacks in the time it once took to coordinate a single campaign. AI models can analyze terabytes of stolen data in minutes and instantly identify high-value targets.
In other words, AI has lowered the cost of launching sophisticated cyberattacks to near zero.
Organizations that raced ahead with AI adoption are now grappling with wider attack surfaces and increased risk exposure. According to Acuvity, 70% of organizations still lack optimized AI governance 🡥, while generative AI data violations 🡥 more than doubled in 2025.
I recently spoke with a major email security provider that analyzes millions of threats per day. Their insight was simple and sobering. Identity has become the new perimeter. More than 80% of phishing attempts now involve AI, including AI-written messages, AI-generated QR codes, and AI-driven MFA bypass techniques.
At the same time, public AI tool usage among everyday employees has doubled. If legitimate adoption is accelerating this quickly, imagine how fast threat actors are moving.
On the dark web today, you can buy ransomware as a service. No technical expertise required. Just a credit card and bad intent.
The result? Powerful attacks are no longer limited to sophisticated attackers.
The bottom line: We’re now in the exploitation phase with AI—and your clients are about to enter the security scramble.
The Reality Your Clients Are Facing
Make no mistake: Business leaders today are under enormous pressure trying to protect their environments and keep up with adversaries.
They are facing threats that move faster than humans can react, with systems that were never designed for this scale of automation.
They’re losing sleep over it.
I know this feeling personally from my time as a CISO. When I started, my environment was 100% on-prem. I understood perimeters, data centers, and server rooms—things I could see and touch.
Then cloud arrived, and suddenly my environment became invisible. But I was still responsible for securing it.
What I was really facing was uncertainty layered on top of complexity. My security budget tripled overnight—but only after a very expensive cyber incident when the damage was done.
As a technology advisor, your role is to help customers confront uncertainty and take decisive action before it impacts their business.
The Security Conversations Leaders Actually Want
Most leaders don’t want more tools. They want someone who understands their business, risk profile, and reality.
When I was a CISO, I hired multiple consultants at various times to advise. I wish I had known about technology advisors who not only advise but are equipped with vendor intelligence, who lean in to understand my business risk, and bring pre-vetted vendors who align with my company’s DNA, risk, and budget.
Your clients need your help to bring clarity into their complex environments. To get you started, here are some easy security conversation starters:
- When was the last time you reviewed your security strategy?
- What worries you most about protecting your business right now?
- Where do you feel confident—and where do you feel uncertain?
- Are you evaluating any security initiatives this year?
These are not technical questions. They are leadership questions and designed to bring curiosity and trust into their challenges and needs.
One Telarus advisor recently had a casual phone call about email security. No presentation. No formal pitch. During that call, he looped in the head of security operations from a large enterprise. That single conversation resulted in a $200K MRR opportunity.
It didn’t happen because of a product. It happened because the partner started a conversation, asked the right questions, and earned the customer’s trust.
What IT Buyers Are Actively Funding in 2026
According to the 2025-26 Telarus Tech Trends report, cybersecurity remains a top priority, driven by data privacy concerns, vendor risk, and regulatory mandates.
Taking a closer look, here are some areas that clients are actively funding in 2026:
- Identity and Access Management (IAM): Policies and technologies that ensure only authorized users and systems can access sensitive resources.
- AI security and governance: Controls that guide how AI is used, secured, and monitored across the organization.
- Zero Trust architecture (ZTA): A security model built on the “never trust, always verify” principle, requiring continuous validation of users and access requests.
- Cloud security platforms: Integrated security solutions that protect data and applications across distributed cloud environments.
The Advantage You Already Have
Security leaders are overwhelmed by sales noise. What they want is clarity, context, and guidance.
As a technology advisor, you’re already approaching customers from a position of strength. You’re not locked into a single platform. You understand their business and risk.
You’ve helped your customers migrate networks, modernize infrastructure, adopt cloud and collaboration tools, voice and UCaaS solutions. You’ve earned the trust and its time to start a security conversation.
Remember: Security leaders are overwhelmed by sales noise. The goal isn’t to sell—it’s to help them build resilience and uncover pain points to identify solutions.

Your Moment Is Now
Now is the time to start engaging customers about cybersecurity, regardless of your subject matter expertise.
Security brings elegance to a conversation because it speaks to leadership, trust, and resilience.
Keep in mind that when selling technology services, security can be a barrier or enabler. Advisors who bring security into the conversation early help customers move faster, deploy more confidently, and unlock additional opportunities.
This week, try reaching out to a few clients with one simple question:
“When was the last time you took a fresh look at your cybersecurity strategy?”
Listen closely. You may be surprised by how open they are about what’s working—and what isn’t.
When concerns come up, you can confidently say:
“That’s something I can help you think through.”
Because you can.
You already understand their business. You already have their trust. This is just a natural extension of the value you’ve been providing them all along.
Security conversations don’t have to feel heavy or intimidating. They can be thoughtful, practical, and forward-looking — focused on helping your clients move faster and smarter with confidence.
There is a real opportunity right now to deepen relationships, open new doors, and become an even stronger partner.
Lean into it. Engage the Telarus team to join your conversation if that seems like a comfortable starting point.
You’re more ready than you think.
Keep the momentum going.
If you want a deeper walkthrough of the trends, the buying cycle, and the discovery questions that work, listen to Sumera’s HITT (High Intensity Technology Training) webinar: 2026 Telarus Cybersecurity State of the Union.